A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.

A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.
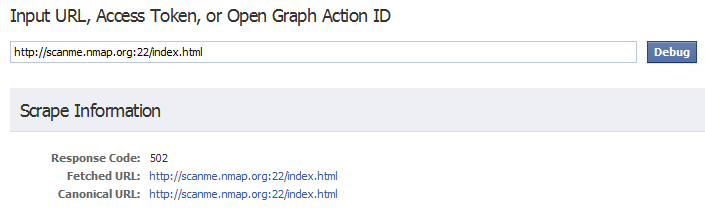
A quick video post showing the XSPA/SSRF bug found with Yahoo! Developer Network. This bug allowed for network port scanning and banner grabbing.

The first XSPA/SSRF bug that led to the discovery of this issue in other applications and eventually a paper that was presented at multiple conferences.
A quick video post showing the XSPA/SSRF bug found with Adobe’s Omniture web application. This bug allowed for local file reads apart from being able to make arbitrary network requests.

This is the third post in the 3 part series that explains XSPA, the attacks and possible countermeasures. In this post we will see other interesting attacks and also see how developers can prevent XSPA or limit the attack surface itself.
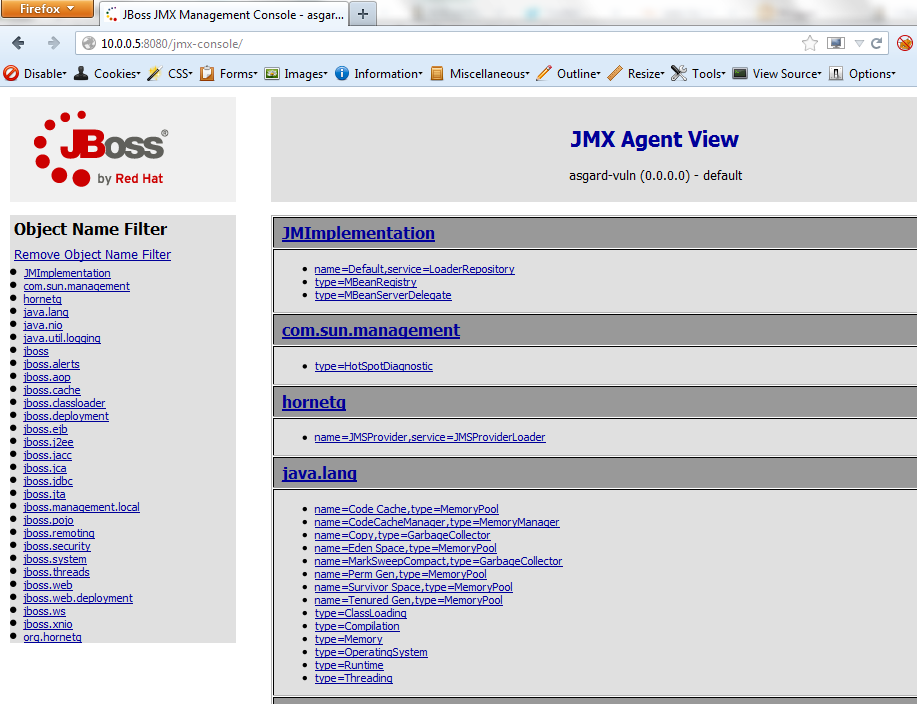
This is the second post in the 3 part series that explains XSPA, the attacks and possible countermeasures.
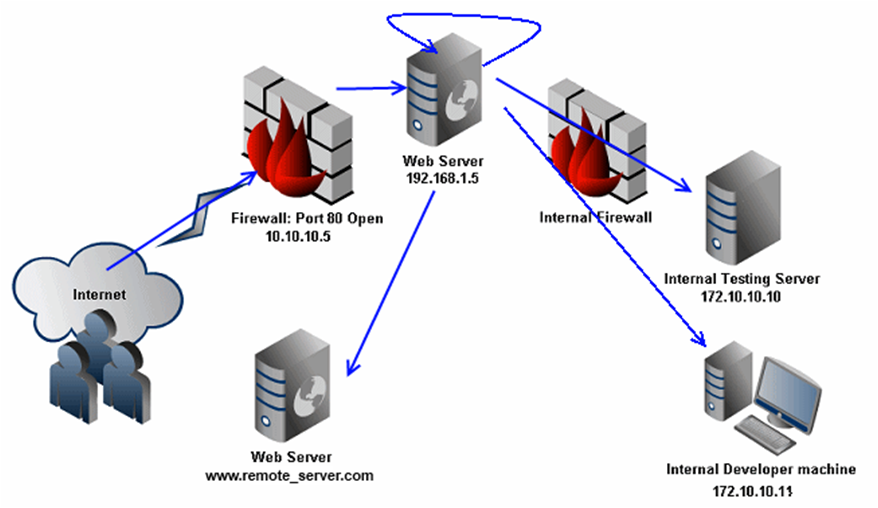
Cross Site Port Attack (XSPA) is a vulnerability that allows attackers to fetch status of TCP ports (and grab service banners) over the Internet or internal systems by abusing a feature in web applications that makes HTTP requests using attacker supplied URLs.