A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.

A blog post about some post exploitation scenarios with MySQL, MSSQL, PostgreSQL and Oracle that use SQL Injection to make network requests resulting in Server Side Request Forgery/Cross Site Port Attacks.
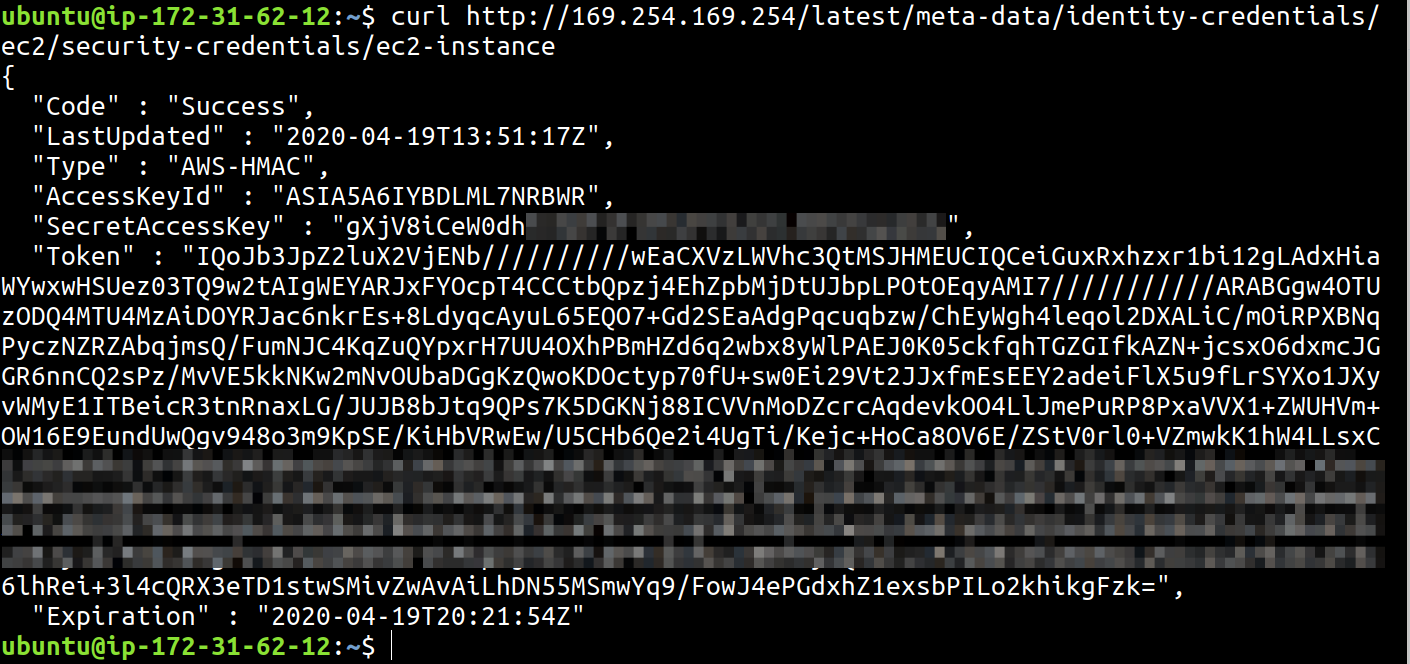
A quick blog post to investigate what instance-identity security credentials are that can be generated using the metadata instance on every EC2 instance in AWS, even when no role is attached to the instance.