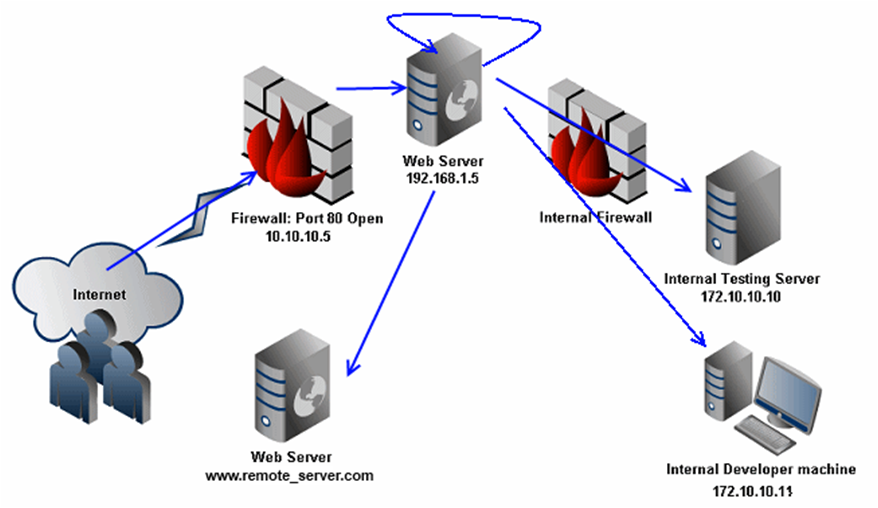
A simple client server Proof of Concept to show how websockets can be used to transfer and execute commands.


A simple client server Proof of Concept to show how websockets can be used to transfer and execute commands.

Creating a auto submit (body onload) form when an input button called submit exists. Very common CSRF exploit PoC.
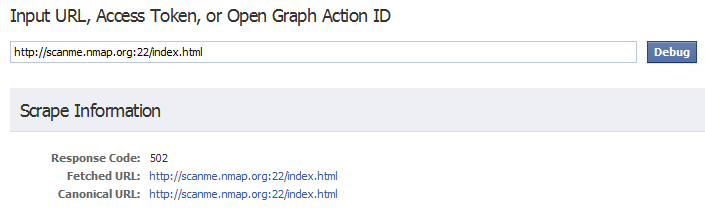
A quick video post showing the XSPA/SSRF bug found with Yahoo! Developer Network. This bug allowed for network port scanning and banner grabbing.

The first XSPA/SSRF bug that led to the discovery of this issue in other applications and eventually a paper that was presented at multiple conferences.
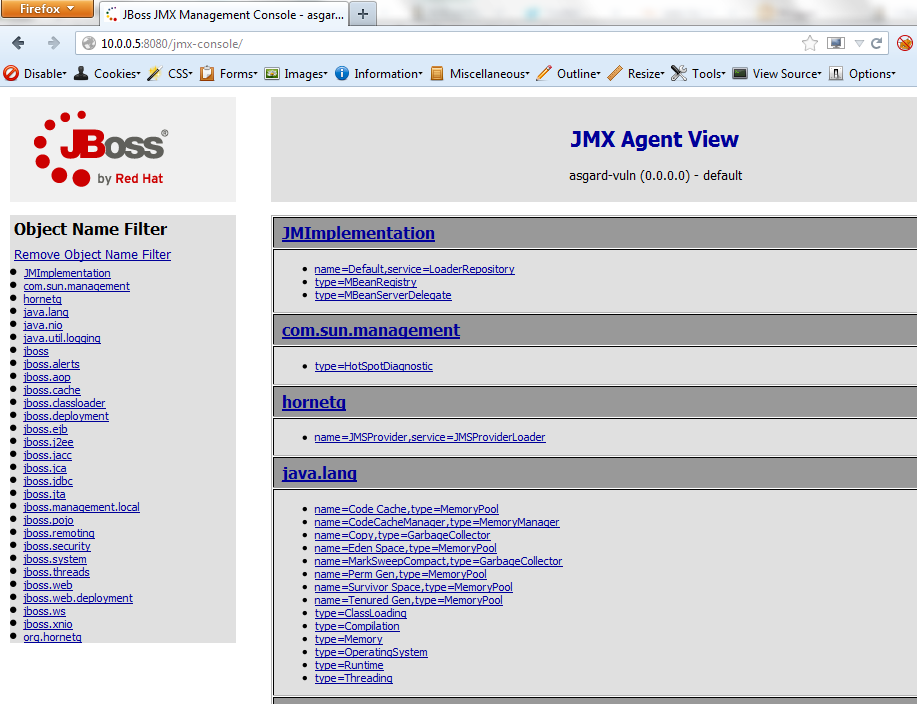
A quick video post showing the XSPA/SSRF bug found with Adobe’s Omniture web application. This bug allowed for local file reads apart from being able to make arbitrary network requests.

This is the third post in the 3 part series that explains XSPA, the attacks and possible countermeasures. In this post we will see other interesting attacks and also see how developers can prevent XSPA or limit the attack surface itself.
This is the second post in the 3 part series that explains XSPA, the attacks and possible countermeasures.