A Windows UAC Bypass using Device Manager
A simple UAC bypass to launch programs using the Device Manager on Windows 10. Requires access to GUI. Limited usage but fun conceptually.
Introduction
Today while working on a Windows 10 machine, I had the need to open the Device Manager for some hardware maintenance. While opening the Windows Device manager I noticed that there was no UAC prompt when I started it. This was a little strange because the Device Manager exists as a Management Console snap-in in %systemroot%\System32\devmgmt.msc and is launched by mmc.exe.
What’s happening under the hood
When you start the Device Manager, mmc.exe is launched with %systemroot%\System32\devmgmt.msc as an argument.
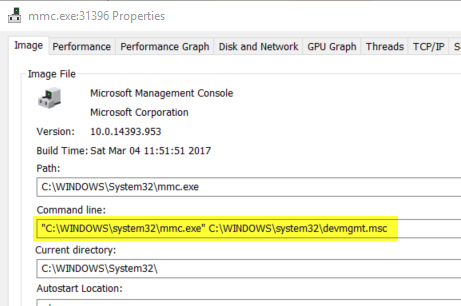
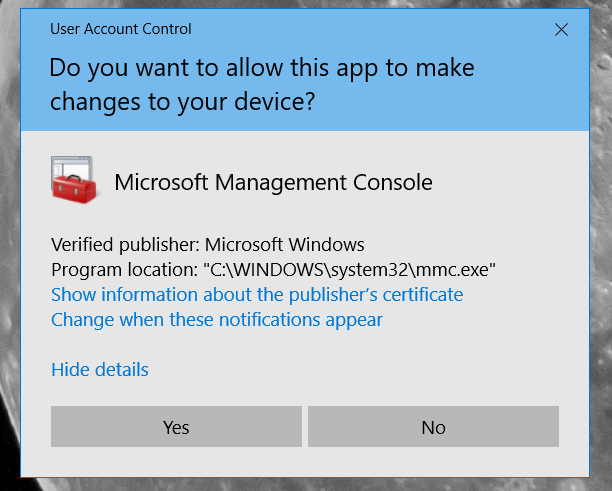
Independently, the Microsoft Management Console requires elevation to run. When you go to run and launch mmc.exe, Windows will ask you to allow elevation using the UAC prompt.
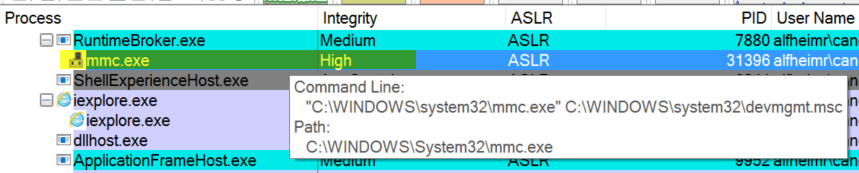
If the Device Manager can be opened without a UAC prompt it means that it was launched with High Integrity level. If this process can be used to spawn other processes, they will be launched with High integrity level too.
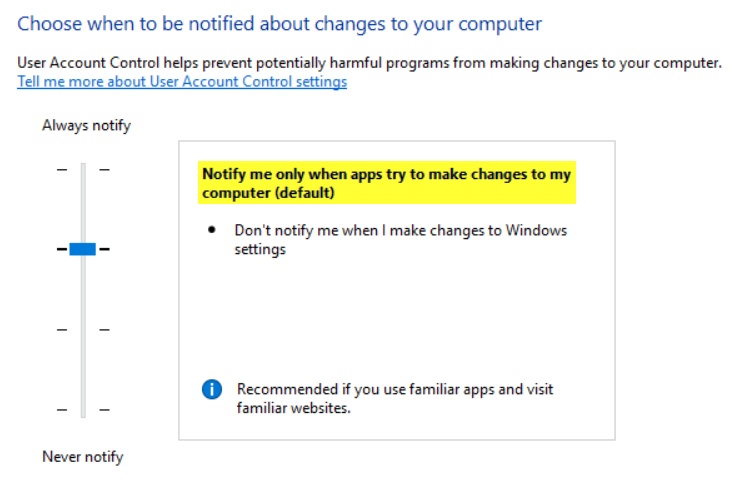
It was trivial from here to find a way to open an elevated Command Prompt without being prompted by UAC. User Access Control on my machine was set to the default value of “Notify me only when apps try to make changes to my computer (default)”
To reproduce this:
- Go to Start run and type devmgmt.msc. Notice that there is no UAC prompt.
- Once the Device Manager opens, goto Help > Help Topics
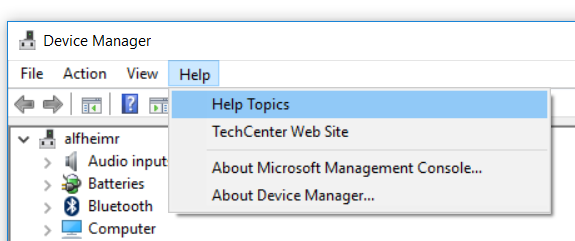
- This will open up the Microsoft Management Console Help window. Right click any where in the right pane and select View Source
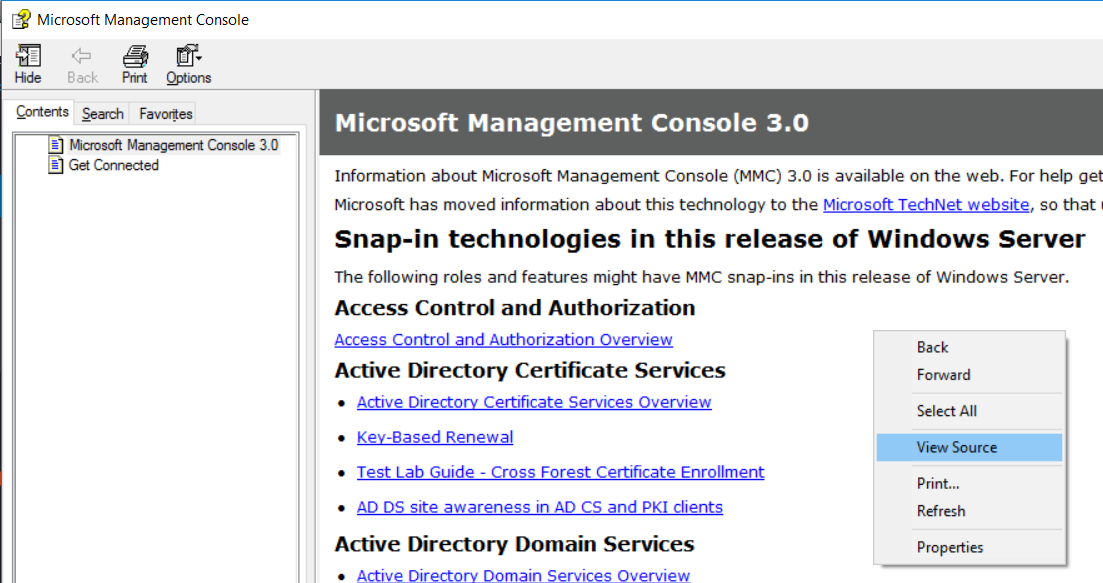
- This will open notepad (the editor may vary if you have set IE’s source viewer to a different text editor).
- Using notepad’s File > Open menu, navigate to the System32 directory.
- Set the File type to “All files (.)” and right click select “Run as Administrator” on
cmd.exe
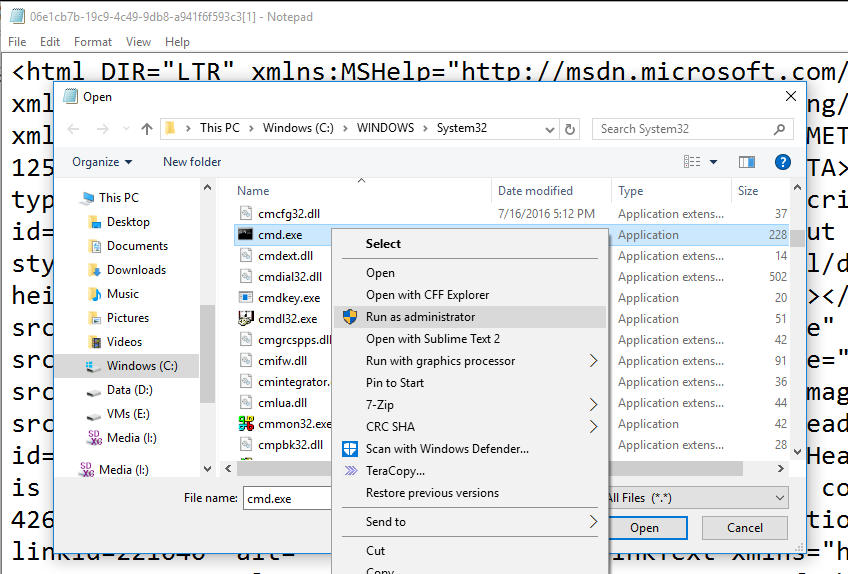
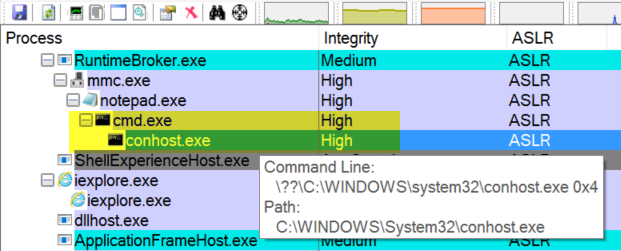
- This should launch a elevated Command Prompt without any UAC prompts. You can run
whoami /privto check that you have a lot of privileges available now (disabled but available). - The process tree also shows that the
cmd.exethat was spawned was started with High Integrity level.
There are several other techniques available on Windows that allow you to bypass UAC and most of them are well documented (see references below). Please note, according to Microsoft, UAC bypasses are not a security problem as UAC is a convenience feature (more references in that page).
Other UAC Bypass References
- https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
- https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
- https://github.com/hfiref0x/UACME
- https://habrahabr.ru/company/pm/blog/328008/ [Use Google translate, worth reading]
Happy Hacking!
