psexec using a local admin account to a UAC enabled system
Enabling the abililty to use psexec over the network when credentials are available by toggling a value in the Windows registry.
Introduction
To protect users across the network, Windows UAC imposes token restrictions on local administrators logging in via the network (using the net use \\computer\\c$ share for example). This means that a local administrator will not be able to perform administrative tasks and will not have the ability to elevate to full admin rights over the network, even when credentials are available.
This works well if you are securing systems. However, during a pentest, hash/password reuse via psexec for example, will fail. Simply because connecting to the C$ admin share to run the psexec service will fail. My friend and systems hacker Anant Shrivastava pointed this out during some testing that he was doing, prompting me to blog about this.
Setup and testing this
I setup a Windows 7 machine with UAC enabled, an administrative account called testadmin with password testadmin and used the exploit/windows/smb/psexec exploit module from metasploit to test this in a lab environment and saw the following error:
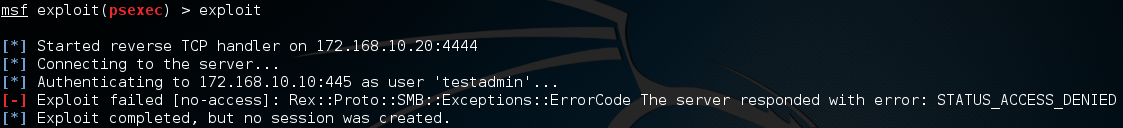
Microsoft recommends a registry edit to disable UAC remote restrictions. To make this change, follow these steps:
- Open the registry editor using the
regeditcommand via Start > Run - Navigate to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System - In the right pane, if the
LocalAccountTokenFilterPolicyDWORD value doesn’t exist, create it. - Set its value to 1 and click OK

The changes take effect immediately. I tried the Metasploit exploit again and voila it worked this time:

This registry change allows Sysinternals Psexec utility to function as well apart from other utilities that require a privileged token on the C$ share (or any other admin share).
Happy Hacking!
